The History of CVEs: From Foundation to the Security Explosion
The Common Vulnerabilities and Exposures (CVE) system has become the backbone of vulnerability management and cyber risk assessment worldwide. Its journey can be divided into three distinct eras: the formative years (1999–mid-2000s), the expansion and integration years (2005–2016), and the explosive growth era since 2016, when the security landscape fundamentally changed.
The Formative Years (1999–Mid-2000s): Building a Common Language
Before the CVE system, security professionals faced a Babel of vulnerability naming conventions. Each vendor and tool used its own identifiers, making it difficult to know if two databases referenced the same flaw. This fragmentation led to gaps in coverage and confusion in incident response.
In 1999, MITRE Corporation launched the CVE project, publishing the first 321 records and introducing a standardized, unique identifier for each vulnerability. This breakthrough allowed IT professionals, vendors, and toolmakers to speak a common language, facilitating interoperability and coordinated responses.
During this period:
- Vulnerability management was largely manual, with organizations relying on mailing lists and direct downloads for patches.
- The first automated vulnerability scanners emerged, but they were primitive compared to modern tools.
- The CVE List quickly became an industry reference, endorsed by the CVE Numbering Authority and adopted by leading security products.
The Expansion and Integration Years (2005–2016): Maturity and Standardization
This era saw the CVE system mature and integrate into the broader security ecosystem. Several key developments marked this period:
- 2005: The U.S. Department of Homeland Security funded the creation of the National Vulnerability Database (NVD), a searchable repository that linked CVEs to severity scores, patch information, and affected products.
- 2007: Introduction of the Common Vulnerability Scoring System (CVSSv2), standardizing how vulnerabilities were rated for severity.
- 2008–2011: Improvements in product and weakness enumeration (CPE, CWE) made it easier to track and categorize vulnerabilities.
- Patch Management Evolution: Vendors like Microsoft and Oracle began regular patch cycles, and automated update deployment became common, reducing the window of exposure.
During this time, the annual number of CVEs grew steadily but remained manageable. The focus was on building robust infrastructure, refining classification, and integrating vulnerability management into enterprise processes. Security teams shifted from purely reactive postures to more proactive scanning and patching, laying the groundwork for modern vulnerability management.
The Acceleration Era (2016–Present): The Security Surge
The CVE landscape changed dramatically after 2016. Several factors triggered an unprecedented surge in vulnerability disclosures:
- 2016: Introduction of CVE Number Authorities (CNAs) allowed vendors and open-source projects to assign CVEs directly, decentralizing and accelerating the process.
- 2017: MITRE streamlined the CVE assignment process, making it easier and faster for researchers to obtain identifiers. This led to a 128% jump in published CVEs in a single year.
- Automation and Scale: Security research, bug bounty programs, and automated scanners proliferated, uncovering more vulnerabilities than ever before.
- Diversity and Complexity: The range of affected products and types of flaws exploded, with hundreds of vendors and new classes of weaknesses identified each month.
By the Numbers:
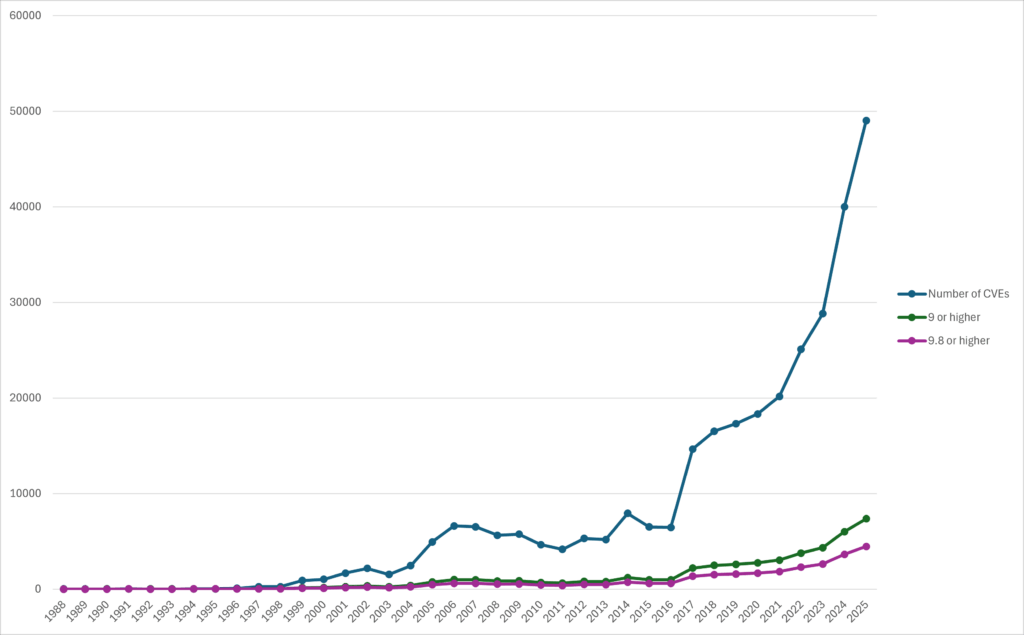
- In 2016, there were about 6,447 CVEs published. By 2017, that number more than doubled to 14,714, and it has climbed ever since.
- 2024 saw a record-breaking 39,987 CVEs published, a 38% increase over the previous year.
- The weekly rate of new CVEs is now over 500, with some weeks surpassing 1,200.
Why the Explosion?
- The growth is not just due to more vulnerabilities being discovered, but also to the ease of reporting and the expansion of the CVE program to more vendors and researchers.
- Modern development practices, cloud adoption, and the proliferation of open-source software have increased both the attack surface and the speed at which vulnerabilities are found and disclosed.
2025 and Beyond: The Next Record in Sight
Based on figures to date, 2025 is on track to set yet another all-time high for CVE disclosures. Current trends suggest that around 49,000 CVEs will be raised in 2025. This would represent a 22.5% increase over 2024, which itself was a record-breaking year.
This continued acceleration highlights both the growing complexity of the digital ecosystem and the increasing effectiveness of the vulnerability discovery and reporting process. Organizations must remain vigilant and proactive, as the volume and diversity of vulnerabilities show no signs of slowing down.
Conclusion
From its beginnings as a solution to a communication problem, the CVE system has become a critical pillar of cybersecurity. The formative years established the foundation, the expansion era standardized and integrated vulnerability management, and the current era is defined by explosive growth and unprecedented visibility. With 2025 set to break new records, the CVE program remains at the forefront of helping organizations worldwide keep pace with an ever-expanding universe of threats.