Fighting the Tyranny of the Default (login)
As the OpenCanary in the Cloud continues to sit with its ports open, waiting for connection attempts, it’s clear to see that a large amount of credentials are being provided to the box as entities on the Internet try to gain access to the system.
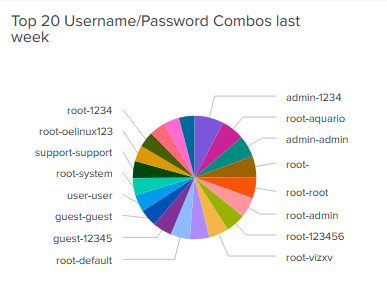
In the last month, there have been close to 400’000 credentials supplied to the honeypot with a significant volume being Mirai-based attacks. Cross-checking the usernames and passwords, 18 of the top 20 username/password combinations seen by the OpenCanary are Mirai/device default logs.

Clearly, there are elements of devices using Mirai code or using the default username/password combinations that Mirai was leveraging that scan the Internet for open ports and try to connect and infect that host. The OpenCanary does not accept any of those credentials successfully – but it does not stop the bad guys and infected devices from trying!
Some integration into the Splunk dashboards is giving a graphical indication of the most common credential combos that the OpenCanary is seeing (on SSH and Telnet, of course).

This will be enhanced to also add a lookup onto a Mirai list – not that it is so relevant since 90% of the Top 20 are those username/password combinations!
Lessons to Learn
It’s extremely simple. If any technology is deployed into any environment, it must be done in a structured and thoughtful manner; firmware update plans need to be in place and all default passwords must be changed.
By having default passwords in place for any network-based asset must be considered a fail in terms of vulnerability management (it’s a configuration item and thus falls into vulnerability and (mis-)configuration management).