In May 2022, I experimented with putting OpenCanary into an Oracle Cloud Ubuntu VM. It was a quick and basic implementation with the following ports open:
- FTP (TCP 21)
- SSH (TCP 22)
- TELNET (TCP 23)
- HTTP (Synology DSM skin, TCP 5000)
I left it to fester and, as I recently implemented a more complete OpenCanary in OCI, I have retired the original one.
It ran for 197 days and the ports lit up 328’347 times….!! The Internet is a dirty. dirty place!

Of the 328’000 attempts to access it, the focus was mainly on getting into the shell of the platform – so SSH and Telnet were the targets. Telnet saw 134’968 connection attempts and SSH 191’563 attempts.
Due to me not having fine-tuned the OpenCanary I was running, I have no credential statistics across those attempts. But fear not – the new OpenCanary I put out there is very popular and I configured it better. I normalised the logs that I captured in 42 hours (17’610 access attempts!)
On Canary 1.0, there were over 25’000 (from 328’000) connection attempts from 61.177.17x.x – guess where these IPs are? Add to that a California-based IP 45.85.147.174 hitting the host 7’800 times and a German IP (176.57.150.175) also hitting the host around that many times.
My top two attacking IP addresses on OpenCanary 2.0 are:
- 49.88.112.75 with 3293 access attempts, apparently some bored child in China
- 111.207.253.232 in second place with 824 attempts (again, in China)
The ports they were hitting were again SSH and Telnet. The spread is close with 9045 hits to Telnet and 8389 hits to SSH. SSH will drop requests due to it not liking the fingerprint, that must be annoying….!
So what about user accounts and passwords they attempt to get into?
- root – 6977 attempts
- admin – 1613 attempts
- default – 403 attempts
- guest – 326 attempts
- user – 131 attempts
I feel a special mention has to go to the user accounts telnetadmin and ubnt; they must be some kind of dumb default accounts on some devices.
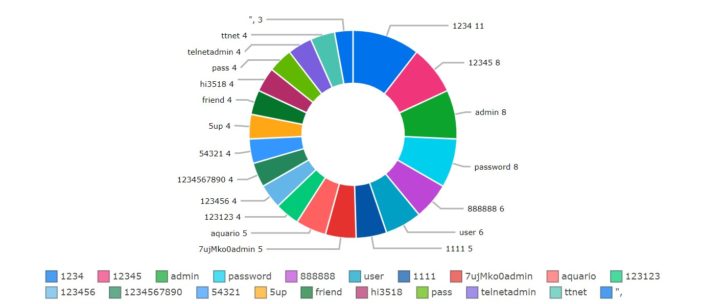
The passwords were interesting.
- 1234/5/6 – the tyranny of the default, no doubt
- Password* – oh yeah….
- admin – more tyranny!
- default, 1111, 888888, 54321 – oh lazy people, where art thou?
- Win1doW$ – it’s an Ubuntu host, I doubt it….
- Zte521 – this must be default on some ZTE kit
Conclusion
It’s clear the Internet is a dirty, dirty place.
OpenCanary is an interesting, free project and hosting it on Oracle Cloud for free is a good experiment. OpenCanary 2.0 is seeing 420 hits per hour and this will lead to some excellent statistics on the ports and protocols being attacked. It is mainly attempts to get a command posture into the system and build from there, that’s clear.
What is also obvious is the combinations of usernames and passwords. Certainly, some of the visits seem to push set credentials into the OpenCanary, Known Dumb Credentials (KDCs). This hints that any default username/password combination deployed to an Internet-facing host will be compromised in hours if not minutes.
One of the key controls that all frameworks have when introducing new technology is to deploy with passwords changed or with other methods, strong methods, of authentication enabled.
Do it – or be a victim.