Phishing for Passwords using FUD
Objects in my spam folder can often be interesting and worthy of investigation. This week, a corker came in under the pretence that it was from ICANN for one of my domains. If you ignore the red flag of coming from sickdisco.com, it certainly can lead to a feeling of FUD.
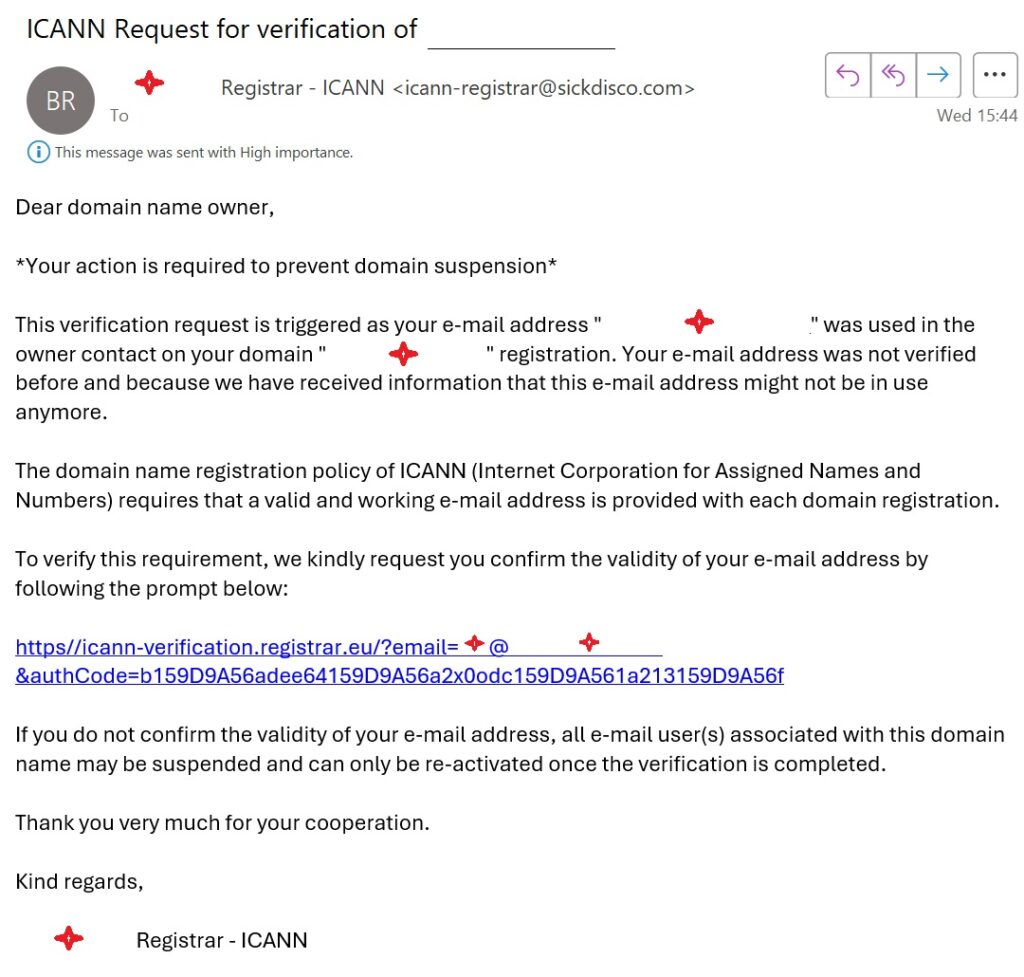
The URL is actually displaying text pretending to be a link to another domain (registrar.eu) but really points to this link (modified for my privacy and for fun):
https://validate.oauth-us.workers.dev/#lee@ohnoiamnotstupid.comHaving changed the URL to not include my phished email (because I get enough spam), I felt it was my duty to follow that new link to see what happens. It redirects to the following URL and displays the image below.
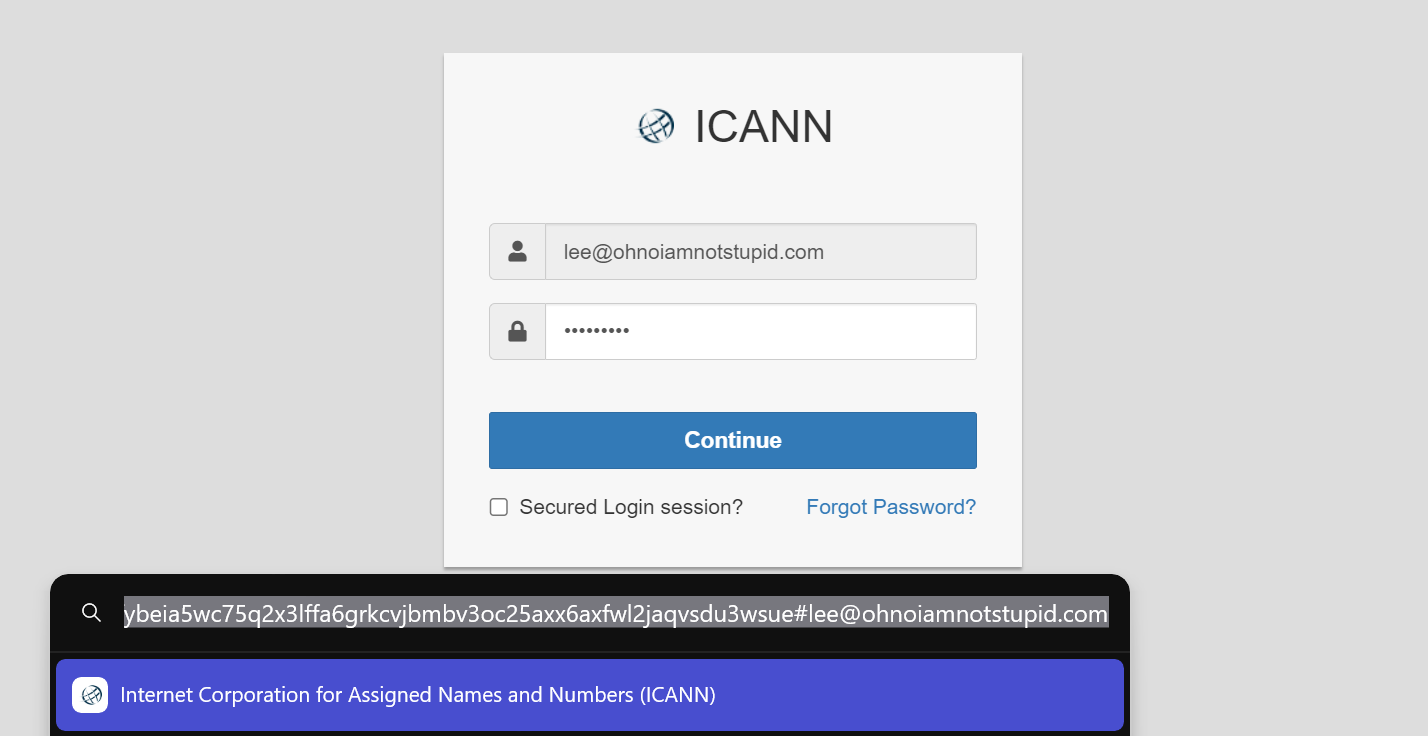
https://gateway.lighthouse.storage/ipfs/bafybeia5wc75q2x3lffa6grkcvjbmbv3oc25axx6axfwl2jaqvsdu3wsue#lee@ohnoiamnotstupid.com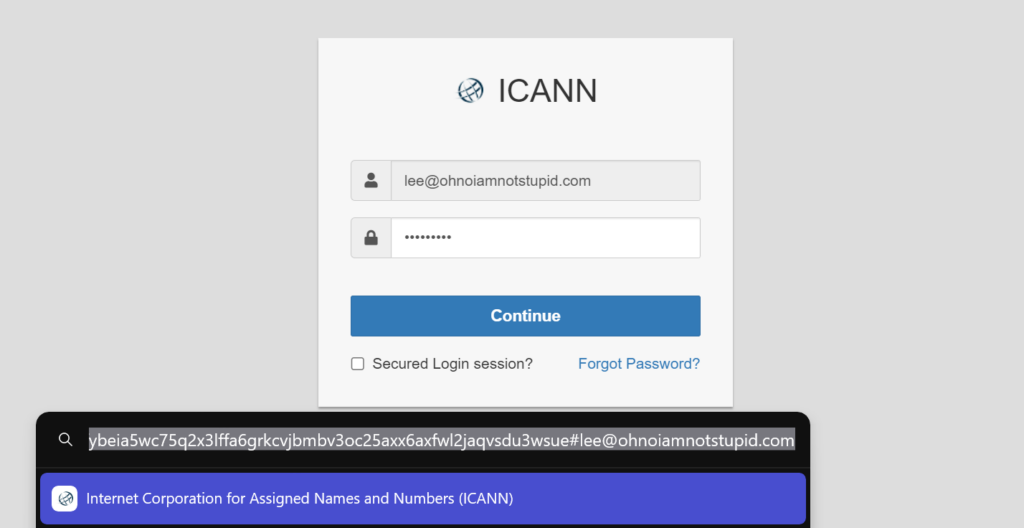
Notice that the website is announcing itself as “Internet Corporation for Assigned Names and Numbers (ICANN)”; this has certainly been copied from the ICANN website – clearly trying to convince the victim that it’s legitimate.
Since the phishing link parses the login name (which is non-editable), all that is left for me is to enter my password. I don’t know what password this could be so entered some text and, since I was feeling comfortable, failed to check the “Secured Login session?” box (what is that anyway`? The connection is over TLS which is free today).
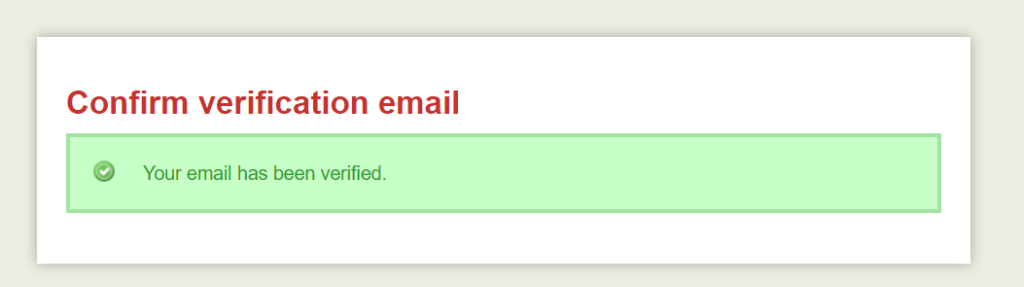
The user journey then actually redirects after some seconds to the ICANN site itself. I guess the email was actually legitimate after all then and I did not give up my username and email password for ohnoiamnotstupid.com (which is available, should you wish to register it).
So “Dear domain name owner”, “if you do not confirm the validity of your e-mail address” – nothing will happen. They are trying to steal your passwords…!!